Forum Replies Created
-
AuthorPosts
-
June 28, 2021 at 2:39 am in reply to: Windows Packet Filter causes file transfer on shares to reduce a lot? #11585
P.S. An example, when I have tested the same machine but the target file was located on the HDD (on the screenshot above the file is on the SSD) I have had about 3x-4x slower throughput with 100% HDD load.
June 28, 2021 at 2:10 am in reply to: Windows Packet Filter causes file transfer on shares to reduce a lot? #11584I have tested 8 years old Core i3-3217U (I don’t have anything slower with Windows installed) sending file to another machine over SMB with and without dnstrace running. Here are the results:
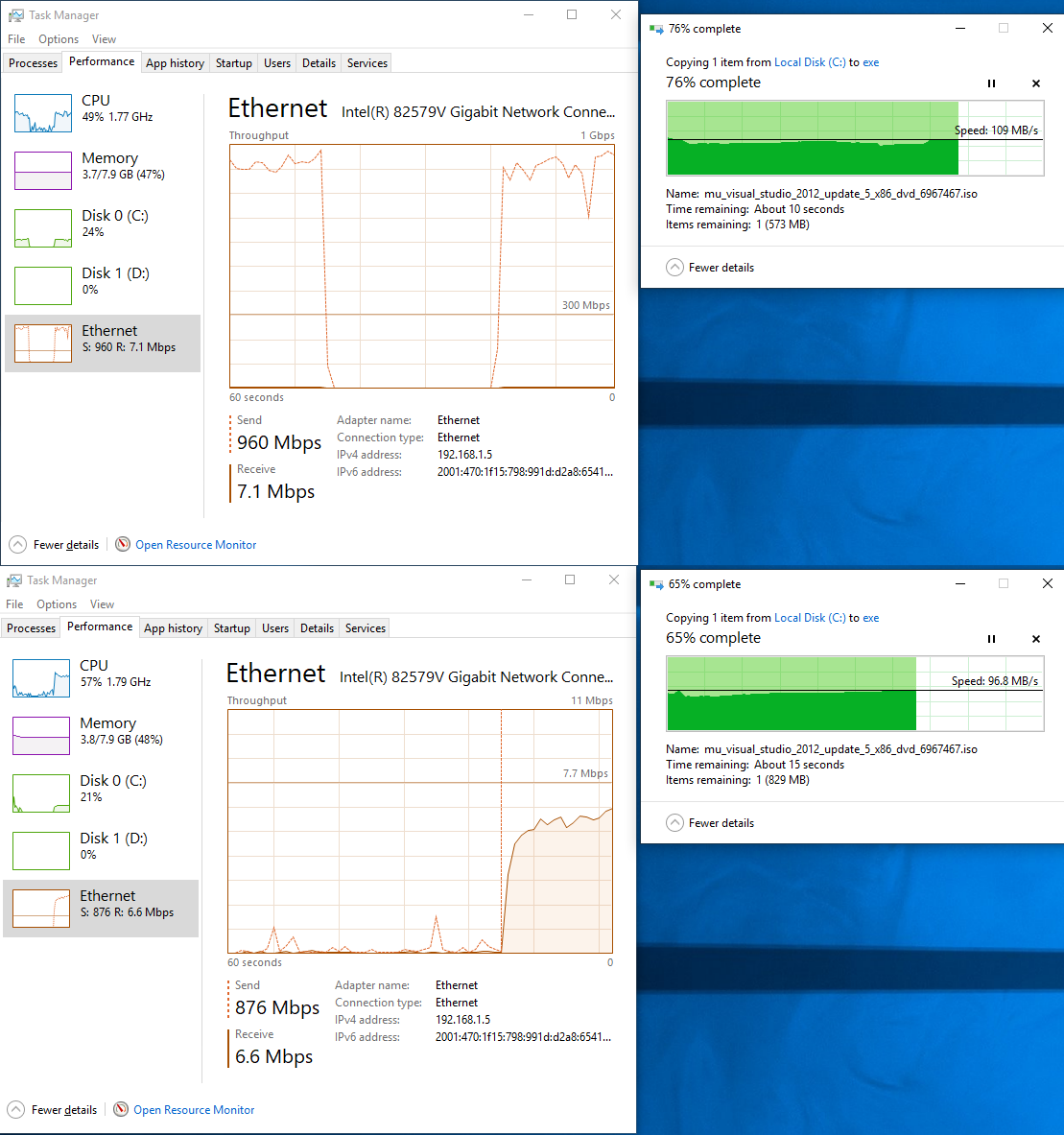
You can notice some slow down (8-9%) but it is not close to the 50% throughput reduction you have reported. What was the bottleneck in your tests?
June 26, 2021 at 10:13 am in reply to: Windows Packet Filter causes file transfer on shares to reduce a lot? #11577Yes, sorry, it is my fault… Saturday evening 😉… In that case traffic has passed over virtual network . Here is the test over the cable:
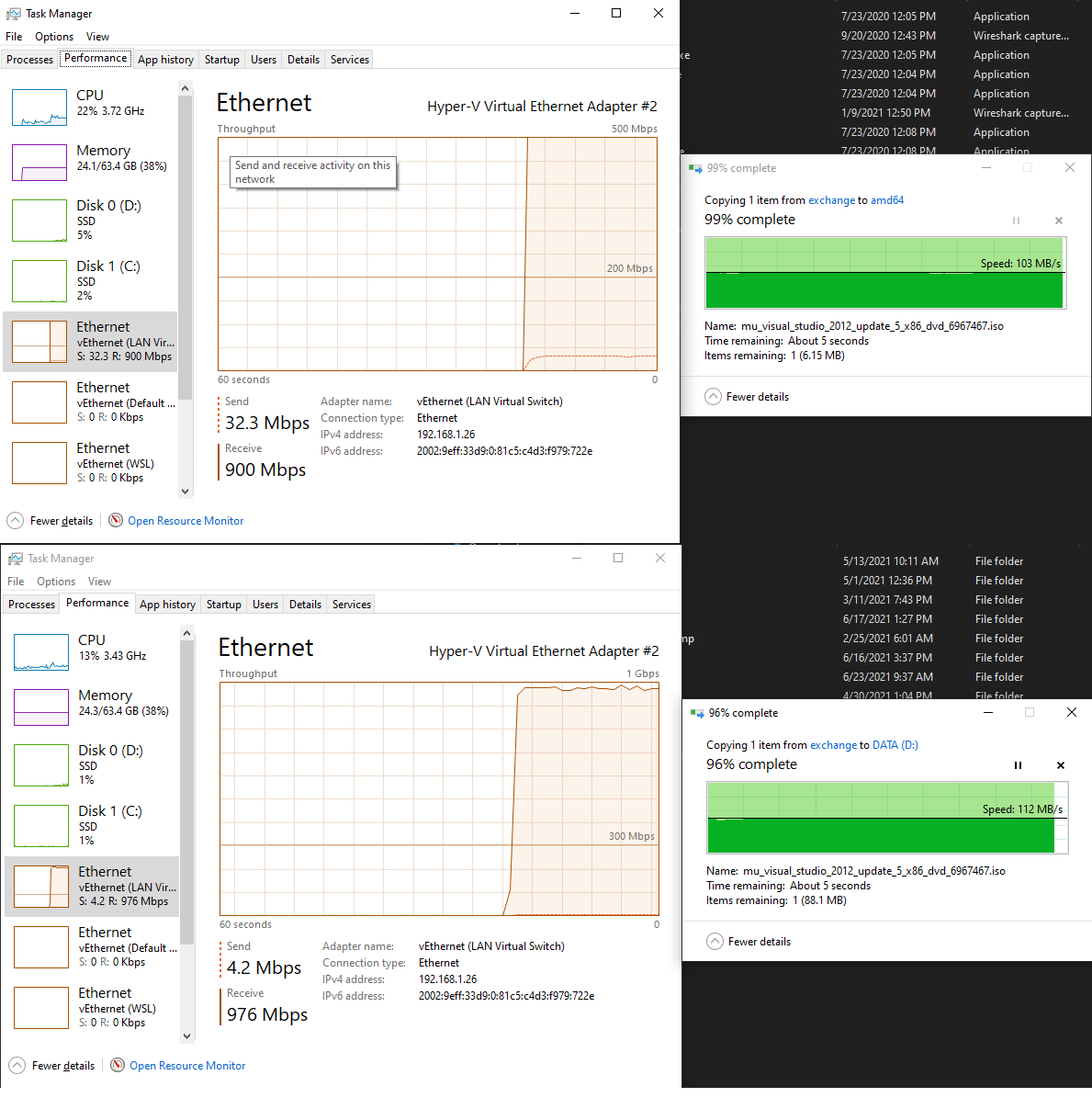
You can notice some bandwidth degradation (900 Mbps vs 976 Mbps without filtering) and extra CPU load.
June 26, 2021 at 9:05 am in reply to: Windows Packet Filter causes file transfer on shares to reduce a lot? #11573Some samples use fast i/o, others don’t, but it is very easy to switch the sample between fast and old model by changing one line of code:
For the Fast I/O:
auto ndis_api = std::make_unique<ndisapi::fastio_packet_filter>(For the ordinary I/O:
auto ndis_api = std::make_unique<ndisapi::simple_packet_filter>(And yes, fast i/o does not support WOW64…
the cpu I’m testing with is core i7 5500
It is fast enough and in my post we have discussed above I have tested much older models. But you have mentioned that you use VM, while I tested on the real hardware over real 1 Gbps wire cable.
June 26, 2021 at 8:36 am in reply to: Windows Packet Filter causes file transfer on shares to reduce a lot? #11569I guess one reason could be because of how powerful the underlying CPU is.
It is easy to verify, just start Task Manager (or Resource Monitor) when you copy the file and check the CPU load with and without dnstrace running. If your CPU peaks even without dnstrace then no wonder if you get the throughput degradation when add extra work…
I want to measure how much overhead this project has if we use it to send every packet to user to check (block or not), and then send those that are OK based on user mode decision. So this dnstrace seems to do exactly this right?
Yes, it filters (takes from the kernel to user space and then re-injects back into the kernel) all packets passed through the specified network interface, selects DNS responses, decodes and dumps.
Can you also try to use the code that was shared on the blog that you mentioned to see if you still don’t get any reduced performance?
Well, dnstrace is good enough to test with. Also, if you would like to test with fast I/O option you can take sni_inspector. It also filters all the traffic for the selected interface, but instead DNS responses selects and dumps the SNI field from the TLS handshake.
June 26, 2021 at 7:36 am in reply to: Windows Packet Filter causes file transfer on shares to reduce a lot? #11565The only idea I have is that you have some other third-party software (which includes NDIS/WFP filter) and somehow results the software conflict… Try to setup two fresh Windows connected over the switch or direct cable.
P.S. To ensure, retested with reversed copy direction and the result is still the same…
June 26, 2021 at 7:25 am in reply to: Windows Packet Filter causes file transfer on shares to reduce a lot? #11563I’ve just taken dnstrace sample (dumps DNS packets and passes everything else without any special handling) and tried to copy one large file from the system running dnstrace to another one. Here is the result with dnstrace running and without:
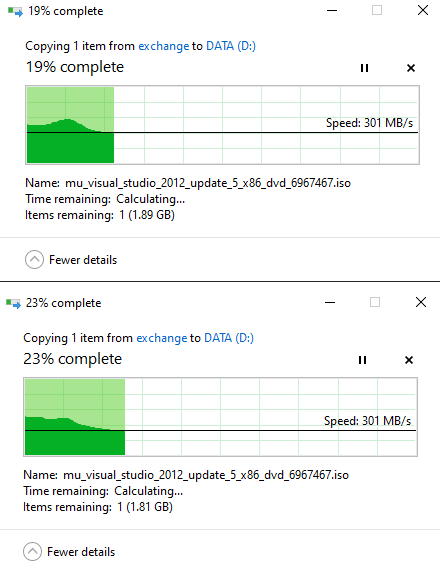 .June 26, 2021 at 6:36 am in reply to: Windows Packet Filter causes file transfer on shares to reduce a lot? #11557
.June 26, 2021 at 6:36 am in reply to: Windows Packet Filter causes file transfer on shares to reduce a lot? #11557The sample code you tested was designed for the demo purposes only. If you are interested in the performance tests you can check this post.
June 26, 2021 at 4:45 am in reply to: Windows Packet Filter causes file transfer on shares to reduce a lot? #11553Capture tool was primarily designed for testing/debugging purposes and it utilizes relatively slow file stream I/O, e.g. each intercepted packet is delayed for the time needed to write it into the file resulting the increased latency and decreased bandwidth.
If you need a high speed traffic capture solution you have to implement in-memory packet caching and write captured packets into the file using dedicated thread instead of doing this in the packet filtering one. Or you could use use the memory mapped file and let Windows cache manager to do the rest 🤔
P.S. And yes, Fast I/O may improve the performance even further…
Windows 10 ARM64 is supported and driver build is available to registered customers.
You can change adapter mode calling SetAdapterMode without stopping the filtering or resetting events. Mode flag only defines what to do with an original packet, in listen mode it is passed over, in tunnel it is dropped.
This one seems to work just fine:
;------------------------------------------------------------------------- ; ndiswg_lwf.INF -- WinpkFilter NDIS LWF driver (WinTun build) ; ; Copyright (c) NT Kernel Resources. All rights reserved. ;------------------------------------------------------------------------- [version] Signature = "$Windows NT$" Class = NetService ClassGUID = {4D36E974-E325-11CE-BFC1-08002BE10318} Provider = %Ntkr% CatalogFile = ndiswg.cat PnpLockdown = 1 [Manufacturer] %Ntkr%=Ntkr,NTx86,NTia64,NTamd64,NTARM64 [Ntkr.NTx86] %ndiswg_Desc%=Install, nt_ndiswg [Ntkr.NTia64] %ndiswg_Desc%=Install, nt_ndiswg [Ntkr.NTamd64] %ndiswg_Desc%=Install, nt_ndiswg [Ntkr.NTARM64] %ndiswg_Desc%=Install, nt_ndiswg ;------------------------------------------------------------------------- ; Installation Section ;------------------------------------------------------------------------- [Install] AddReg=Inst_Ndi Characteristics=0x40000 NetCfgInstanceId="{ACAA7086-8B4C-4443-B5CE-9694A907670C}" Copyfiles = ndiswg.copyfiles.sys [SourceDisksNames] 1=%ndiswg_Desc%,"",, [SourceDisksFiles] ndiswg.sys=1 [DestinationDirs] DefaultDestDir=12 ndiswg.copyfiles.sys=12 [ndiswg.copyfiles.sys] ndiswg.sys,,,2 ;------------------------------------------------------------------------- ; Ndi installation support ;------------------------------------------------------------------------- [Inst_Ndi] HKR, Ndi,Service,,"ndiswg" HKR, Ndi,CoServices,0x00010000,"ndiswg" HKR, Ndi,HelpText,,%ndiswg_HelpText% HKR, Ndi,FilterClass,, compression HKR, Ndi,FilterType,0x00010001,0x00000002 HKR, Ndi\Interfaces,UpperRange,,"noupper" HKR, Ndi\Interfaces,LowerRange,,"ndis5,ndis4" HKR, Ndi\Interfaces, FilterMediaTypes,,"ethernet, wan, ppip, bluetooth, ndis5, nolower" HKR, Ndi,FilterRunType, 0x00010001, 1 ;this filter must run before any protocol can bind to the below miniport ;------------------------------------------------------------------------- ; Service installation support ;------------------------------------------------------------------------- [Install.Services] AddService=ndiswg,,ndiswg_Service_Inst [ndiswg_Service_Inst] DisplayName = %ndiswg_Desc% ServiceType = 1 ;SERVICE_KERNEL_DRIVER StartType = 1 ;SERVICE_SYSTEM_START ErrorControl = 1 ;SERVICE_ERROR_NORMAL ServiceBinary = %12%\ndiswg.sys LoadOrderGroup = NDIS Description = %ndiswg_Desc% AddReg = NdisImPlatformBindingOptions.reg [Install.Remove.Services] DelService=ndiswg,0x200 [NdisImPlatformBindingOptions.reg] HKR, Parameters, NdisImPlatformBindingOptions,0x00010001,2 [Strings] Ntkr = "NT Kernel Resources" ndiswg_Desc = "WinpkFilter LightWeight Filter for WinTun" ndiswg_HelpText = "WinpkFilter NDIS LightWeight Filter for WinTun"Try to add ‘ndis5’ to the list and let me know if it helped.
Windows Packet Filter NDIS filter driver does not bind to WinTun network adapter because of the following in wintun.inf:
HKR, Ndi\Interfaces, LowerRange, , "nolower"while in ndisrd_lwf.inf we have:
HKR, Ndi\Interfaces, FilterMediaTypes,,"ethernet, wan, ppip, bluetooth"So there are two choices:
- Change wintun.inf ‘nolower’ to ‘ethernet’
- Add ‘nolower’ to the list of FilterMedia types in ndisrd_lwf.inf
As a side effect second option will cause Windows Packet Filter driver binding to the interfaces it normally would not bind to and therefore it is not supported by stock driver build.
Then there must be something wrong with your modified SYN packet. Enable checksum verification in Wireshark and check if packet checksums are good.
-
AuthorPosts
