Forum Replies Created
-
AuthorPosts
-
The requested extended parameter to exclude applications (DisallowedApps) was added in v.1.1.16. Please give it a try.
There are three small features that I would like to add to the next version. I hope to be ready in a week or two, depending on whether I have enough spare time.
If you have IPv6 enabled and use an IPv6 DNS (e.g. iPhone hotspot) then no traffic goes via the tunnel.
Could you please collect the wiresock application log and PCAP files for this setup and can send the files/link to [email protected]? It should help me to understand what is going on.
We can check what is going on by analyzing log and PCAP files:
Troubleshooting
If you experience any problems, then first try starting the application/service with ‘-log-level all‘ command line parameter. If you run it as an application, then it dumps the debug log directly on the console, while service will save the log into the file located in C:\ProgramData\NT Kernel Resources\WireSock VPN Client. In both cases, all processed network packets will be stored in PCAP files (can be opened and analyzed in Wireshark) in the C:\ProgramData\NT Kernel Resources\WireSock VPN Client.Please note that ‘-log-level all‘ exists for debug purposes only and significantly affects the application performance.
Typically, if the system is configured with both IPv4 and IPv6 DNS, DNS queries are sent to both. Thus, most applications should work fine. Please check if browsers are working good via wiresock and the only problem you are having is with using nslookup.
The latter seems to always default to an IPv6 DNS address if available, and this is where we have some issues.
It looks a bit unusual that a laptop has an IPv6 DNS server but no IPv4. However, this is quite a possible setup. I think I’ll just add IPv6 to IPv4 and vice versa DNS resolution to close this question.
Yes, that explains what’s going on. Wiresock does not change your network settings or add another DNS server from the WG configuration. Instead, it translates and forwards DNS requests to the DNS server from WG configuration instead of the original one. But it does not convert IPv4 DNS requests to IPv6 and vice versa. I’ll think about what can be done about it. However, if your laptop is configured with an IPv4 DNS server in addition to an IPv6 server, then all other applications (such as browsers) should work fine. NSLOOKUP should also work fine if you manually set the DNS server to any IPv4 address. For example, using
server 8.8.8.8or any other IPv4 address will force nslookup to use the DNS server from the WG configuration.Thanks for the details. One question though, how nslookup works without WG (stock or wiresock) activated? Does it try to use the IPv6 DNS servers?
Hmm, while standard WireGuard adds a virtual NIC with an assigned IP address along with the appropriate DNS servers, Wiresock implements the same using Network Address Translation (NAT). For example, the outgoing DNS request is NAT translated to the DNS server taken from the configuration file. However, meanwhile, an IPv4 DNS query is only translated to IPv4, and IPv6 is only translated to IPv6. There is no address translation between IPv4 and IPv6 DNS queries.
I’m not 100% sure, but I suspect your case may be related to these IPv4/IPv6 DNS server differences. If you’re interested, we could analyze this issue in more detail to find a workaround.
P.S. You can try disabling IPv6 on your mobile hotspot to see if this is the case.
In the current version, this is not possible, but I think it makes sense to add such an opportunity.
Yes, it does!
Meanwhile, there is no such tool. When I have spare time, I plan to add a simple user interface for Wiresock VPN Client to provide basic information about tunnel status, IP address, etc.
I also noticed that when I starting the service, the TUN network adapter does not appear, as it did normally when the wireguard client was started.
WireSock does not add a virtual network adapter, NAT and encryption are applied to packets on the fly. This is very similar to how the Cloudflare WARP client works.
[SOCKS5]: S2C_AFTER: 4.0.0.0 : 2304 -> 192.168.1.105 : 64262 etc.
This is my fault, I didn’t test the configuration when both SOCKS5 and Wireguard are running on the same IP. Please download update v.1.1.5 and check how it works.
It looks like you have a firewall in between that is blocking SOCKS5.
If this is the case and if you are interested in further research, I think we could find & add another suitable method instead of SOCKS5.
It’s really weird. It looks like you have a firewall in between that is blocking SOCKS5. Web browsers use SOCKS4 by default, and maybe that matters. To clarify, could you please capture the Dante traffic on the server side? For example, for my test machine in Oracle cloud:
ubuntu@instance-20211213-2206:~$ sudo tcpdump -D 1.ens3 [Up, Running] 2.lo [Up, Running, Loopback] 3.any (Pseudo-device that captures on all interfaces) [Up, Running] 4.bluetooth-monitor (Bluetooth Linux Monitor) [none] 5.nflog (Linux netfilter log (NFLOG) interface) [none] 6.nfqueue (Linux netfilter queue (NFQUEUE) interface) [none] ubuntu@instance-20211213-2206:~$ sudo tcpdump -vv -i ens3 -w file.pcap port 1080 tcpdump: listening on ens3, link-type EN10MB (Ethernet), capture size 262144 bytes 11 packets captured 11 packets received by filter 0 packets dropped by kernelThe resulted capture in Wireshark:
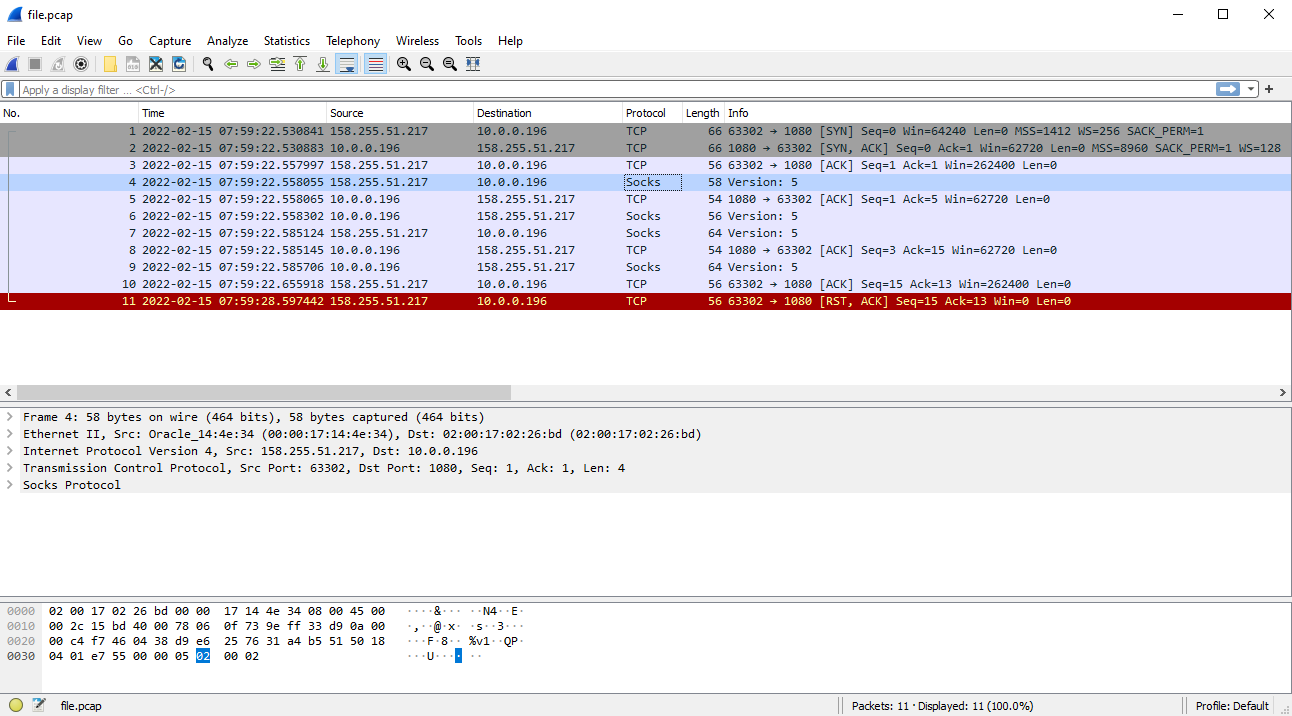
-
AuthorPosts
