
In a sense, this article is a continuation of a series of materials about implementing a WireGuard client based on Cloudflare BoringTun and a custom packet filter for Windows. This approach differs from the conventional method used in most VPN clients, which typically rely on a virtual network interface. Instead, WireGuard integration here occurs entirely in userspace, with packet interception and injection directly into the Windows network stack.
This architecture offers a number of clear advantages:
- High performance;
- No need to modify system routing tables;
- Ability to run on top of an existing VPN connection;
- Isolation and predictable behavior.
For those interested in this type of architecture, it’s worth noting that a similar approach was recently implemented in ExpressVPN for Windows — within their Lightway Turbo protocol, which interacts directly with the network, bypassing the Windows TCP/IP stack.
That said, this article focuses on another aspect — once again discussing WireGuard protocol blocking and the available countermeasures. With the rise of DPI systems and mass VPN protocol blocking in several countries, more and more users are looking for ways to circumvent censorship. One such solution is AmneziaWG — an obfuscation layer built on top of WireGuard, developed as part of the Amnezia VPN project.
I received a number of requests to add support for AmneziaWG to WireSock Secure Connect, and this feature was recently implemented. In this article, I’ll break down how AmneziaWG works, where it shines, where it falls short, and in what cases it’s actually needed.
What is AmneziaWG
AmneziaWG is a modification of the WireGuard protocol designed to complicate traffic analysis by DPI systems. Compared to vanilla WireGuard, AmneziaWG implements several layers of obfuscation:
- It injects junk packets before the handshake, effectively warming up the UDP connection and creating background noise before the VPN tunnel is established. This option can be used independently of the server type and works perfectly with standard WireGuard.
- It modifies packet type tags, making them less recognizable to DPI systems.
- It adds junk data into the handshake, masking it by size so it doesn’t stand out due to predictable length.
Of these three methods, only the first works with standard WireGuard and does not require any protocol modification. The other two affect the cryptographic hash, meaning they require low-level changes in implementations like WireGuard-go, BoringTun, and others.
Architectural remarks
In my opinion, the current AmneziaWG approach isn’t the most elegant from an architectural standpoint. Tag and handshake modifications could be applied after encryption — externally to WireGuard — in the form of a standalone proxy. This would bring the following benefits:
- Ability to use faster implementations like official WireGuardNT instead of patched WireGuard-go with built-in obfuscation;
- Easier maintenance — no need to patch drivers or libraries;
- A more flexible architecture, allowing obfuscation to be enabled/disabled at the routing layer.
That said, what’s done is done. To some extent, AmneziaWG has become a “de facto” standard, and so I implemented support for it as a separate BoringTun branch and integrated it into WireSock.
Self-hosted usage and practical observations
In real-world use, self-hosted AmneziaWG shows solid reliability and resistance to blocking. With handshake masking and tag obfuscation, traffic becomes harder for DPI systems to fingerprint — especially in countries with aggressive filtering.
If you want to deploy AmneziaWG on your own VPS, it’s very easy using a community-made script called amneziawg-install.
⚠️ Before installation, it is strongly recommended to:
- Upgrade your system to the latest version;
- Reboot your server.
Step-by-step setup:
Download the script via curl or wget:
curl -O https://raw.githubusercontent.com/Varckin/amneziawg-install/main/amneziawg-install.shwget https://raw.githubusercontent.com/Varckin/amneziawg-install/main/amneziawg-install.shMake it executable:
chmod +x amneziawg-install.shThen run it:
./amneziawg-install.shThe script will ask a few questions and then:
- Install the AmneziaWG kernel module and tools;
- Configure the server;
- Create a systemd service;
- Generate a client configuration.
To manage clients (add/remove), just re-run the script.
The resulting config can be used in clients like WireSock Secure Connect, Amnezia VPN, or any other app that supports AmneziaWG.
Simple obfuscation with junk packets
However, in many scenarios, full AmneziaWG functionality may not be necessary. A lighter and more universal method of obfuscating VPN traffic is the injection of junk packets in standard WireGuard. This technique does not require protocol or library changes and can be implemented entirely in userspace, making it easier to deploy and maintain.
The idea is to add pseudo-random UDP packets before or during the VPN session, creating “noise” around the handshake and data transfer. This helps reduce DPI detection accuracy and can bypass simpler filters.
This method is effective against many real-world blocks, especially when the provider does not use complex behavioral analysis or stateful DPI.
Real-world example: bypassing Cloudflare Warp blocking
One good example is the blocking of Cloudflare Warp in Russian ISP Rostelecom’s network. Although Warp uses WireGuard under the hood, the provider identifies and cuts off the handshake.
However, by injecting junk packets into a standard WireGuard config (e.g., generated via wgcf), the blocking can be bypassed. Junk traffic support is already implemented in many clients, including WireSock Secure Connect, where it can be enabled without any changes on the server side.
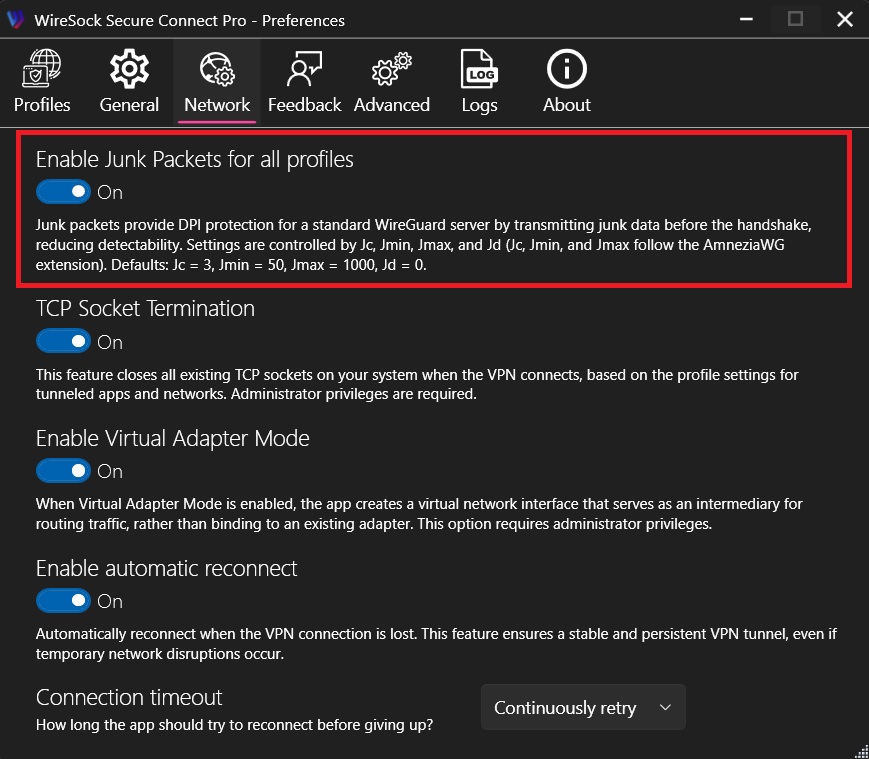
This approach is especially useful:
- When using public or third-party servers where AmneziaWG installation is not possible;
- When needing to switch quickly between profiles or infrastructures;
- On resource-constrained devices where simplicity is key.
In short, junk packet injection is a fast and simple way to harden WireGuard against blocking — often sufficient without resorting to more complex solutions.
Conclusion
As filtering tightens and DPI adoption grows, more users are searching for flexible, reliable, and technically sound ways to retain internet access. AmneziaWG is one such tool, providing effective resistance via handshake and packet structure modification. I give full credit to the developers who made this possible and freely available to the community.
That said, I still believe that implementing it as a standalone proxy would have been more flexible and easier to integrate across platforms.
At the same time, many scenarios are well covered by simpler solutions like junk packet injection in plain WireGuard — easier to implement, less infrastructure-dependent, and suitable for most practical use cases.
Adding AmneziaWG support to WireSock Secure Connect brings additional flexibility — especially for users operating under heavy network restrictions — without sacrificing performance or ease of use.
If you’re curious about the client architecture, want to discuss implementation details, or just exchange practical insights — join our community:
We’ll be happy to hear your experience, questions, and suggestions!
