Windows Packet Filter (WinpkFilter©) is a high-performance packet filtering framework for Windows that allows developers to transparently filter (view and modify) raw network packets at the NDIS level of the network stack with minimal impact on network activity and without having to write any low-level driver code.
Windows Packet Filter includes NDIS 3.1/4 hooking VxD driver (Windows 95/ME), NDIS 4 hooking filter driver (Windows NT/2000/XP), NDIS 5 Intermediate (Windows XP/2003) and NDIS 6 Lightweight Filter (LWF) drivers as well as companion user-mode API DLL and samples.
A key advantage of Windows Packet Filter in comparison to other packets filtering frameworks for Windows (based on Windows Filtering Platform (WFP) callout drivers, Layered Service Providers (LSP), TDI filters etc…) is the ability to manipulate raw Ethernet frames achieved by installing driver below all network protocol drivers and just above network interface driver. Thus, WinpkFilter driver has an ultimate control over all network traffic flow destined to or originated from your system and allows you to modify any packet, drop it or even forge and insert an entirely new one. Using Windows Packet Filter requires no experience in kernel mode programming on your behalf, since it provides you with a powerful user level API. However, if you need to implement your solution (to achieve better performance) in kernel mode, you can do that as well by adding your functional code directly to Windows Packet Filter driver’s code.
System Requirements
| Windows 95/98/Millennium | Windows Server 2008* | Windows Server 2012 R2 |
| Windows NT 4.0 | Windows 7 | Windows 10 |
| Windows 2000 | Windows Server 2008 R2 | Windows Server 2016 |
| Windows XP | Windows 8 | Windows Server 2019 |
| Windows Server 2003 | Widows Server 2012 | Windows 11 |
| Windows Vista* | Windows 8.1 | Windows Server 2022 |
The following connections types are supported for the operating systems above:
- Wired Ethernet (802.3)
- Wi-Fi (802.11)
- WAN (Analog/ISDN modems, PPPoE, 3G/4G mobile modems)
- Mobile Broadband (PPIP)
Product features
- Reliability and stability confirmed by hundreds of satisfied customers since product launch in 2002 ranged from small shareware companies to world known corporations.
- High performance. WinpkFilter allows handling Gigabit network bandwidth in user mode application without noticeable performance degradation.
- Complete and easy portability across all Windows desktop platforms.
- Operates on RAS/PPP adapters and supports Windows 7 Mobile Broadband stack(PPIP)
- Passive network listening (collecting network packets) and active filtering (with capability to edit/drop network packets) modes
- Interface for injecting raw Ethernet frames into the network stack (either destined from the TCP/IP to the network and in reversed direction)
- Support for MTU decrement (allows setting system-wide MTU decrement). This option is useful if you plan to add additional headers to IP packets (implement IP in IP packet tunneling, IPSEC based VPN and so on).
- The powerful built-in network filters engine allows setting rules to pass, block or redirect a network packet to a Windows Packet Filter-based application for further processing.
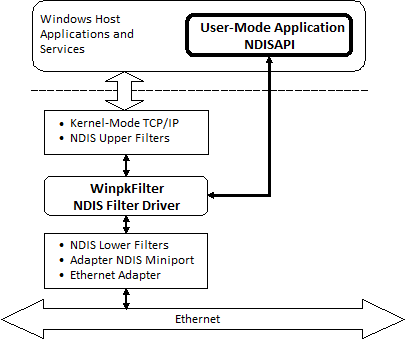
Applicability/Usage Scope
Windows Packet Filter can be used as a base for the following kinds of network applications (including but not limited to):
- User-mode firewall and content filtering solutions. No more need to write kernel mode drivers to implement the firewall!
- Kernel-mode firewall and content filtering solutions. This requires kernel-mode programming skills and Source Code license (to integrate your network packet processing code directly into the drivers) but provides the maximum possible performance.
- Internet Connection Sharing (Network Address Translation) that can be implemented either in user or kernel depending on performance requirements.
- Virtual Private Network solution (IPSEC, SSL VPN, Wireguard etc.) that can also be implemented both in user and kernel depending on performance requirements.
- Network packets tunneling solution. An example, packets captured from the network can be tunneled from the client to the remote system inside the SSL, SSH, HTTP, ICMP etc., extracted by the remote host and injected into the real network (after required packet headers modifications). Response packets can be returned to the client in the same manner. This may allow bypassing certain network access limitations.
- Packet sniffer. You can capture and inspect all packets sent to (received from) TCP/IP.
- IP shaping solutions (when you need to limit bandwidth for Internet users).
- Network traffic counting and bandwidth management solutions.
- Wireless Firewall Gateways, even with HTTP authorization.
- Transparent proxy solution based on NDIS level packet redirection. This can be used, an example, to decrypt SSL(Man-In-The-Middle), parent content control, e-mail SPAM filtering etc…
- Transparent filtering bridge
